Change Store Email Addresses - Mageplaza
How To Stop Brute Force Attacks in Magento 1, 2
Vinh Jacker | 04-06-2016

Brute force attacks are becoming very common these days. Most websites are vulnerable to such break-in attempts. The fact that these attacks give severely negative impacts on online stores - million or even billion dollars can be lost, personal data can be misused and violated - rings an alert to store owners. E-commerce business doers seriously care about solutions to get rid of this threat.
If you use Magento, they are located at /admin and /downloader by default and can be abused in several ways. Hackers can easily find them and launch a brute-force attack. In such an attack, random passwords are tried automatically, until one succeeds.
A brute-force attack is one of the simplest methods to gain access to a website because other than patience it does not require any additional skills or resources. Brute-force attacks are simply trial and error. During an attack, certain permutations and combinations of usernames and passwords are used by hackers to attempt to break into an account.
To save your store from being attacked, just spend a couple of minutes reading the following solutions. Also, Mageplaza provides a security extension to help you auto-tighten security for your store 24/7.
6 Solutions to stop Brute Force Attacks in Magento 1, 2
- Solution 1: Customize the admin path
- Solution 2: Secure your Magento admin account
- Solution 3: Protect /downloader folder
- Solution 4: Secure .git folder
- Solution 5: Keep your store up-to-date
- Solution 6: Enable HTTPs for the admin panel
- Solution 7: Enable CAPTCHA function
- Solution 8: Enable Two-Factor Authentication
Solution 1: Customize admin path
The default Magento 1 backend url is your-domain.com/admin. Because the default Magento backend URL is common knowledge in brute-force suites, you can easily get some advantages by cutting the low-hanging fruit.
Customize your current admin path as the following:
Edit file /app/etc/local.xml
XML Path: admin -> routers -> adminhml -> args -> frontName
You can see <![CDATA[admin]]>, now change it to your own admin url, e.g: secret or mybackend
Now flush Magento cache to take effect: System -> Cache Management -> Flush Magento Cache
Magento 2: Not required.
Solution 2: Secure your Magento admin account
2.1. Don’t use the admin account
People usally use admin as their first admin account. This is security issue for your Magento store because hackers can guest it easily. We recommend that you should change the admin account name to your own account name, nickname or your email address.
2.2. Keep your password strong
The best way to protect your Magento store against a brute-force attack is to – and advise other administrators to – use a strong password. An adequate password should:
- Contains more than 8 characters
- Includes numbers
- Includes characters (Using both lowercase and uppercase characters is highly recommended)
- Includes symbols: optional
Solution 3: Protect /downloader folder
In Magento 1, it uses /downloader called Magento Connect Manager folder to install extensions from Magento Marketplace. This is the default path, it is easy for hackers to attack your Magento website. You can rename it but there is an effective way to protect the downloader folder, it is IP whitelist
3.1. Apache
Edit the file downloader/.htaccess and add the folowing lines to the end:
order deny,allow
deny from all
allow from x.x.x.x
x.x.x.x is your whitelist IP v4 address.
3.2. Nginx
Open configuration file of your Magento website.
E.g: /etc/nginx/conf/mywebsite.conf
Add the following block of lines:
location /downloader/ {
allow x.x.x.x;
deny all;
location ~ \.php$ {
echo_exec @phpfpm;
}
}
3.3. Cpanel or DA hosting
You can ask for support from your hosting providers. You may also seek our Magento support to address any specific platform-related issues.
Tips: Choose a great hosting for your Magento 2 store.
3.4. Protect local.xml file
local.xml file is very sensitive data that contains database information, admin path or crypt key.
If this information is leaked to the public, you will run into serious problems.
Check it now, navigate your browser to http://your-domain.com/app/etc/local.xml
If it cannot access the data, your website is safe. Otherwise, you can follow the Protect /downloader folder to disable that.
Solution 4: Secure .git folder
Github is now popular, every store is using Github as the control version of its store. Git folder contains many important information such as repo url, code files …
You can follow the Protect /downloader folder to disable that.
Solution 5: Is your store up-to-date?
Apply security paches. There are some security patches that Magento has released recently, you can download it here
- Install the Magento latest version. Updating to latest version will keep your store healthy.
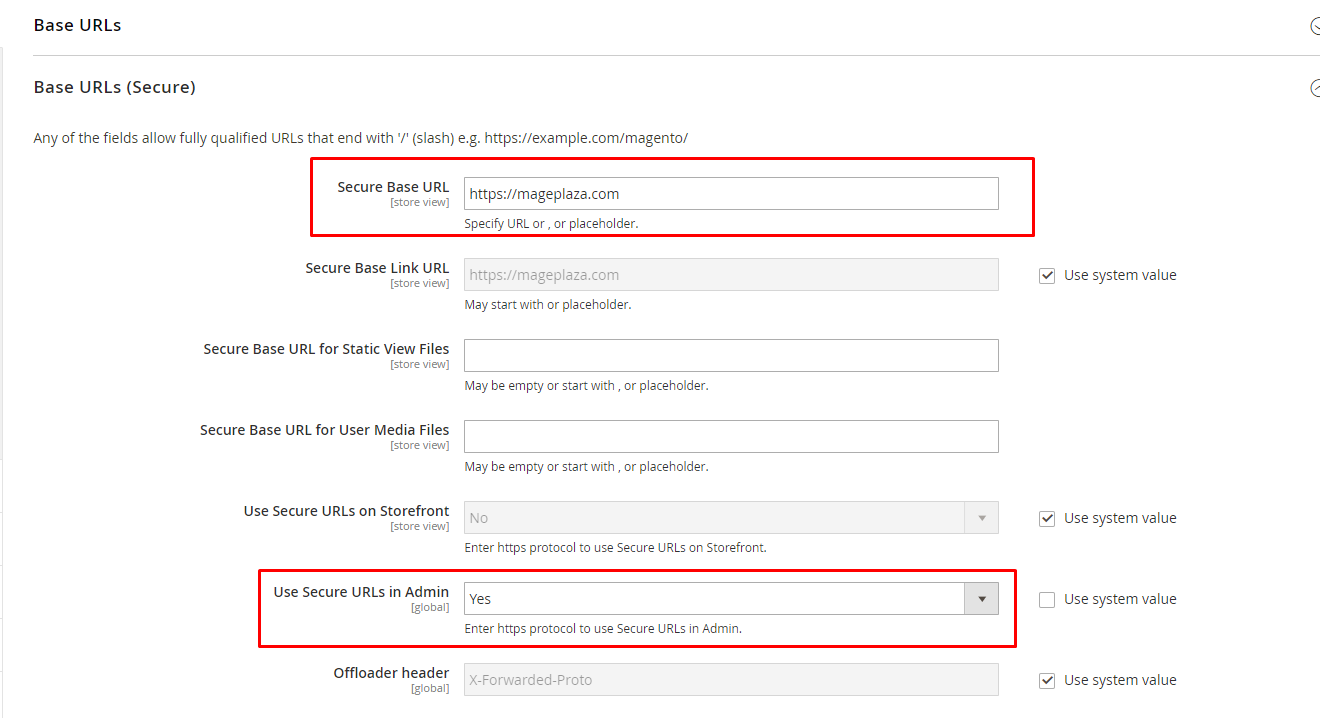
Solution 6: Enable HTTPS for admin panel
Since Magento is used for e-commerce transactions, the data is often very sensitive. This is why it is recommended that all of your login details should pass through a secure connection.
Go to Stores > Configuration > Web
Solution 7: Enable CAPTCHA function
CAPTCHA involves code combinations of letters and numbers, serving the purpose of distinguishing human actions from automated bot activities.
To prevent multiple login attempts through Brute-force attacks in Magento, implementing CAPTCHAs is a recommended security measure.
To safeguard their admin panel from automated brute force assaults, merchants are advised to activate CAPTCHA.
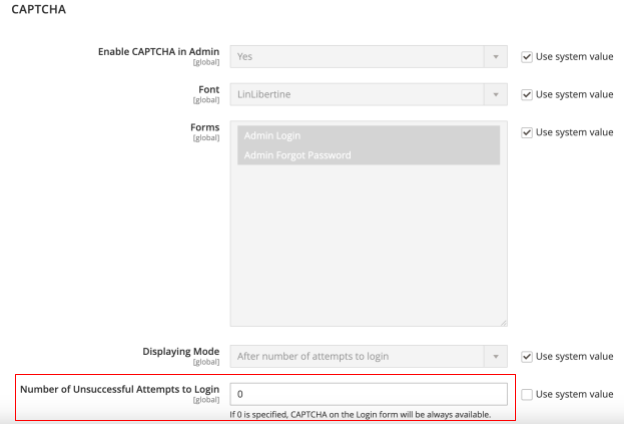
Follow the path Stores > Settings > Configuration > Advanced > Admin > CAPTCHA.
Additionally, ensure the CAPTCHA option Number of Unsuccessful Attempts to Login is set to 0 (zero).
By implementing these steps, CAPTCHA verification will be mandatory for all admin login attempts.
Solution 8: Enable Two-Factor Authentication
An efficient strategy to thwart brute force attacks is the adoption of Two-Factor Authentication (2FA), which helps restrict login attempts.
Magento’s Two-Factor Authentication involves a two-step verification process, introducing an extra layer of security for accessing the Admin UI across all devices.
The configuration of Two-Factor Authentication in Magento can be carried out through command-line installation. This additional security measure enhances protection against unauthorized access attempts.
The bottom line
Brute Force Attacks can happen in both Magento 1 and 2 and may affect your store security negatively. Hope all the solutions provided above can help you protect your store better. Don’t forget that we also have a free tool to help tighten your security called Mageplaza Security for Magento 2. Check it out and send us messages if you need more support.
Related Post








